Coding Vulnerability Insight
SQL Injection Vulnerability Overview
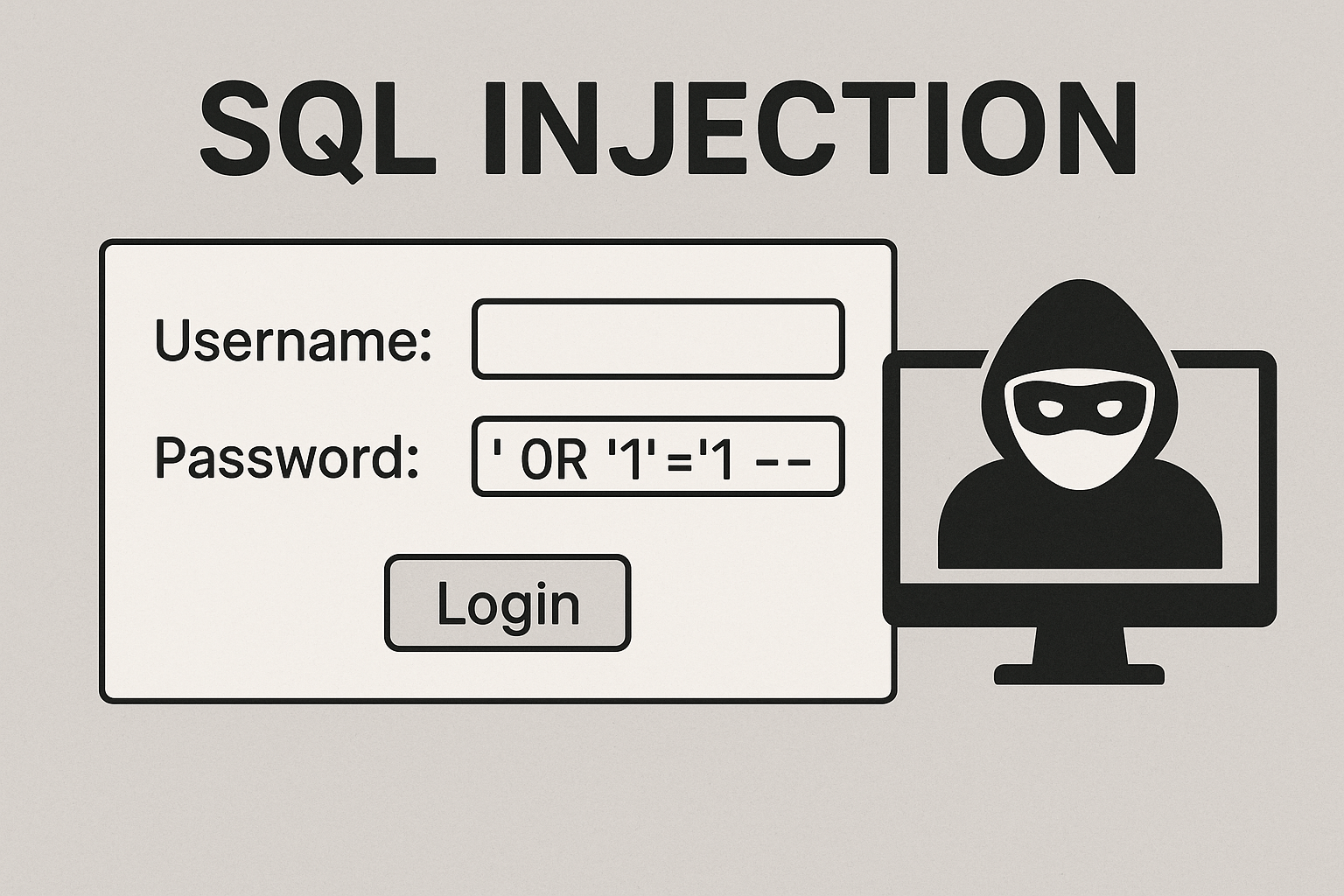
**SQL Injection** is a critical security vulnerability that allows attackers to manipulate SQL queries through user input fields. This visual highlights a common example where a login form is exploited using the payload ' OR '1'='1 --. By injecting malicious SQL code, the attacker bypasses authentication and gains unauthorized access to the database. SQL injection occurs when applications fail to properly sanitize or validate user input before including it in SQL statements. This vulnerability can lead to data breaches, unauthorized data manipulation, and full system compromise. Moreover, SQL injection is consistently ranked as one of the most dangerous web application threats by OWASP. To mitigate this risk, developers should use prepared statements, parameterized queries, and input validation techniques. Therefore, understanding and defending against SQL injection is essential for securing web applications and protecting sensitive data.
Key Features of SQL Injection
- Exploits Input Fields: Attackers insert malicious code via text boxes or query strings.
- Bypasses Authentication: Common payloads allow access without valid credentials.
- Compromises Data: Enables unauthorized read, update, or deletion of database records.
What’s Included with SQL Injection Explanation
- Example of a vulnerable login form and SQL injection attack.
- Hacker illustration representing the threat of input exploitation.
How to Prevent SQL Injection
- Use prepared statements (e.g.,
PreparedStatementin Java orparameterized queriesin Python). - Validate and sanitize all user inputs before using them in SQL queries.
- Apply least privilege principles and avoid exposing unnecessary database functions.
Ideal Uses and Placement
- Use in security training, vulnerability awareness posters, and developer onboarding guides.
- Ideal for teams focused on DevSecOps, backend development, or application hardening.
SQL Injection Specifications
- Attack Type: Input-based code injection
- Payload Example:
' OR '1'='1 -- - Risk Level: Critical (unauthorized access, data leakage, full control)
Explore More Resources
- Find secure coding tools: Products Page
- Learn about app security: Our Blog
- Secure your backend: AI & QA Resources
- Official OWASP Resource: OWASP SQL Injection Guide
Why Choose This SQL Injection Guide?
SQL injection remains a top threat to application security. Moreover, it’s easy to exploit and devastating if unaddressed. Therefore, this guide is essential for every developer and security team.
Protect Your Code Today!
Stop threats at the source—learn how to identify and defend against SQL injection attacks now!
$3.99
- ✅ Instant Download Available
- 🖼️ Ultra High-Resolution 4K PNG + JPG (4096×6144, 300 DPI)
- 🖨️ Prints Beautifully up to 13.6×20.5 inches
- ♾️ Unlimited Downloads
- 🔁 Commercial Use & Resale Allowed
- 💾 Digital Product – No Physical Item Shipped
- 📥 Instant Access via Download Link Post-Purchase
- 🛒 Want a Physical Print?
You can upload your downloaded artwork to services like Printful, Zazzle, or your local print shop to create stunning physical prints.
All 4K images include the label "4K" in their title.
If your selected image does not include "4K", please contact us for your complimentary upgrade.